IT security at the highest level – with Zero Trust Security from NCP
Businesses face cyber threats to their IT infrastructure every day. Many organizations are now planning IT security through a Zero Trust strategy to deal with evolving attack vectors. Zero Trust Security from NCP is a perfect fit in this scenario.
What does Zero Trust mean?
Zero Trust is not a product, it is a general IT security approach that follows the principle of least privilege. Instead of trusting users and end devices blindly, Zero Trust ensures that users are only granted access to the data they need to do their current work. Zero Trust systems run in the background and check whether a user is authorized each and every time they access data.
How is Zero Trust different from other IT security concepts?
The Zero Trust approach leaves cybercriminals little room to maneuver, as even a successful attack can only gain access to a small part of the entire company network. Compromised network resources can be isolated and the threat neutralized without having to shut down the entire system.
How does the NCP Zero Trust Security solution fit within a Zero Trust strategy?
NCP’s software-based IT-security solutions are built on Zero Trust. Unlike other products, NCP offers holistic network security, rather than just a secure connection to the company network. With NCP Secure Enterprise Management (SEM), IT administrators can configure access rights for user groups and individual users granularly. Through centralized access management, the NCP security solution fits seamlessly into the Zero Trust principle.
Why choose NCP's Zero Trust Security solution?
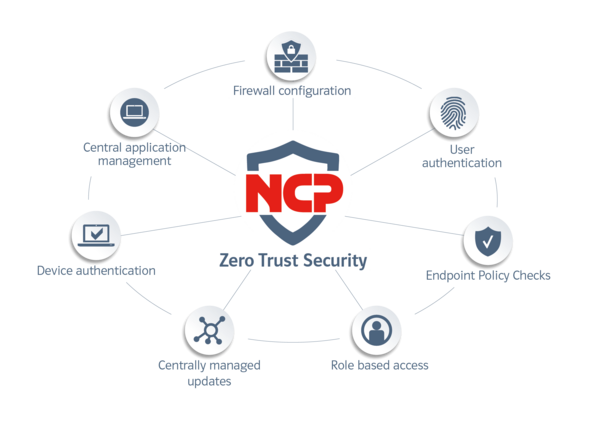
Device authentication
Use unique device authentication methods such as machine certificates or endpoint policy checks to reliably prevent access by non-company or insecure devices.

User authentication
Secure your users' logins with multifactor authentication (MFA) or user certificates, for example. Together with the features of the corresponding end devices, you create fully comprehensive security identities for maximum security.

Firewall configuration
Define individual firewall settings that effectively secure each workstation without much effort.

Centrally managed updates
Distribute policies, changes and software updates with just a few clicks - either for individual users, user groups or the entire organization. This means that even large numbers of users can be kept up to date quickly and easily!

Endpoint Policy Checks
Check the up-to-dateness of virus scanners, OS updates or machine certificates of end devices and thus prevent potential entry gates.

Role based access
Assign your users to freely definable user groups and adjust access rights as desired - per user group or granularly at user level. Keep control over unauthorized user access!

Central application management
In our central management software, you define exactly which users, groups and applications can access which network resources. Attackers thus have no chance of unauthorized system access.